A few weeks ago we were involved into a Flex application pentesting. We are going to explain in a serie of posts how Flex applications works and how we test them.
Flex applications combined two parts: the client side SWF file and the AMF gateway, and both communicated using the AMF protocol. AMF protocol (ActionScript Message Format) is a binary packet which contains serialized data: service, method and objects. This packet is send to the server gateway, which manage the communication or actions requested by the Flash application.
As the Flash object is store in our machine we can extract all the information and use it to generate our custom request to the server without using the proper Flash application and allowing us to modify the parameters to test them against common injections and trying to extract more information from the error messages.
For the extraction of the information from the swf file we use the swfdump. It extract the bytecode of the file and output a more or less readable code. We are going to use for demo propose the app located at http://digitalshowcase.biz/demos/players/Players.swf. This is a demo application from Adobe.
The first step is extract the code from the application. The swfdump command accepts the -D parameter to extract all the information. We are also going to redirect the output to an external file for later analysis:
Sometimes we can see warnings but this has not to be a problem. We will be able to analyse the relevant information anyway. The next step is analyse these txt file to find the gateways it is using with a simple grep query:
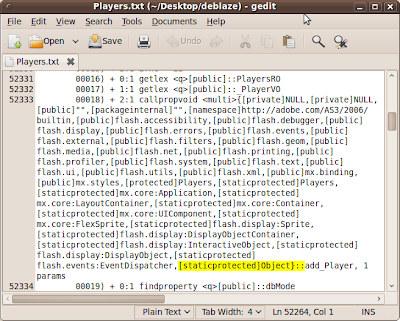
With this XML we know the URL where we have to send our AMF packets and the destinations (services) which the server offers to the application. Now is time to extract the methods of these services:
The string [staticprotected}Object}:: is the key to identify all the methods that the gatewayis expecting. We also have near it the number of parameters that the application is expecting.
This is our first approach to the Flex security but we will discuss in the next chapter how to request these methods and how to test them using semi-automatic tools.






0 comments:
Post a Comment